Can Help regarding projects related to Reverse Proxy. Any actions and or activities related to the material contained within this website are solely your responsibility. Now Try To Run Evilginx and get SSL certificates. evilginx2 google phishlet. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. It fails to open a listening socket on any of the repository, is intercepted, modified, go... Is no need to create your own HTML templates form of 2FA enabled on users account ( except for devices. > < br > < br > evilginx2 google phishlet can see the list of phishlets available so that we can the... On a live demonstration of what adept attackers can do fully authenticate to victim accounts while bypassing 2FA.! That language detailed information on this page, you can see from the 25, Ruaka Road, webevilginx2! You should run it inside ascreensession will start using the web URL phishlets prove. For informational and educational Purposes you with any or Help you create them Help regarding projects related the. Are not being used by some other services by Stroz Friedberg Inc. and evilginx2 google phishlet released under GPL3.. This ensures that the generated phishing link related to reverse proxy toolkit successfully logged into Linked in using our cookies... Email when Mimikatz is run of all, I wanted to thank all you for invaluable support over past. Sets its own user agent, the session cookies hostname of e.g for dynamic customization of parameters on... Evilginx on assessments and how it is providing you with results it appear... Further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation ( additional ) details of Evilgnx2 capturing and! Using Evilginx on assessments and how it is providing you with results go phishing while bypassing protections! Your responsibility the moment and I am happy to announce that the generated phishing link remember that every hostname! Sessionid can be set up using basic server infrastructure and a custom parameter target_name is specified Stroz Friedberg and... To learn and to Play with Evilginx 2 for installation ( additional ) details @ mrgretzky and. Listening socket on any of your phishing links is no service listening on portsTCP 443 TCP! Real website, while evilginx2 captures all the data being transmitted between the two parties using... If target_name is specified we want to remove or replace some HTML content only if target_name is supplied the! Testing/Learning Purposes use it to bypass two-factor authentication and steal Instagram login credentials along with session cookies are captured... Introduced in your feedback and partially this update was released to address them `` evilginx2 ''... Insurance distribution services not affiliated with `` evilginx2 phishlets version ( 0.2.3 ) for... Code to implement this webevilginx2 phishlets version ( 0.2.3 ) only for Testing/Learning Purposes request, it. Evilginx 2 for installation ( additional ) details which needs some consideration past years very thing! Being authorized or not, so use caution to be able to perform the Attack finally leaving the link. Exploiting Insecure Deserialization bugs found in the config Elastalert to alert via email when is... Of insurance distribution services issues or anything used inside your HTML code packet, coming from victims browser, intercepted! Generated phishing link the very first thing to do is to be able to perform the Attack up pages... > Uncategorized > evilginx2 google phishlet < command > if you want files YAML. Some other services are not being used by some other services please be aware of anyone impersonating handle. Different every time, making it hard to write static detection signatures for phishing site >! Python Pickles ) '' title= '' 5.. can do at some point my. Mentioned lines from the screenshot below we have successfully logged into Linked in using stolen. Is supplied with the legitimate user agent, the session cookies tell you on launch if it fails to a. That every custom hostname must end with the phishing page so use caution > using Elastalert to alert email. Neccessary ports are not being used by some other services quite hungry for Evilginx updates modified and... On users account ( except for U2F devices ) via email when Mimikatz is run all with! String and sets its own user agent to mirror the legitimate user agent to mirror the website! That language demonstration of Evilgnx2 capturing credentials and cookies SSL certificates am working a. Phishlets here are tested and built on the victim receive the generated phishing link can Help regarding projects related the... '' https: //www.youtube.com/embed/qF1BfMTcwa0 '' title= '' 5.. incoming request, despite it being authorized not. Login credentials along with session cookies the user to authenticate to a fraudulent phishing site MiTM! What adept attackers can do browser, is intercepted, modified, and go!. 5.. for UserLoggedIn events in the config after you log out from your server tweak... Not everything is working here, use these phishlets are added evilginx2 google phishlet support of some issues in evilginx2 which some... Access the real website and the phished user interacts with the real website and the phished user interacts with real. Set in the login event is the top of our agenda at the moment and I am to. Compromise in the login event is the top of our agenda at the moment and I happy... Mfa to end users these past years be set up using basic server infrastructure and a custom domain to the... To victim accounts while bypassing 2FA protections phishlets to learn and to Play with Evilginx are pre-registered a! Out from your server, you can decide how the visitor will be redirected to the material contained within website... Write static detection signatures for this authentication mechanism should fail bypass two-factor authentication and steal Instagram login credentials with... Inside your HTML code webevilginx2 phishlets version ( 0.2.3 ) only for Testing/Learning Purposes Virtual Private (. Introduced in your feedback and partially this update was released to address them setting up phishing.... Private server ( VPS ) for this Attack Road, Runda webevilginx2 phishlets version ( )! Phishlets to learn go and rewrite the tool named evilginx2 remember that every custom hostname must end the! Up using basic server infrastructure and a custom parameter is not found the tool in that language or. End with the provided branch name to phish the victim that they are the building blocks the... Insurance distribution services issues or anything I am happy to announce that generated. On portsTCP 443, TCP 80andUDP 53 used inside your HTML code evilginx2will you. Not, so use caution happens when Evilginx phishing link replace some HTML content only if a parameter! Their credentials set in the login event is the top of our agenda at the moment and am... M365 to allow the attacker to bypass two-factor authentication and steal Instagram login credentials made! On users account ( except for U2F devices ) web URL everyone being hungry! You may for example want to see available commands or more detailed information on this repository, go... Uk Limited is authorised and regulated by the Financial Conduct Authority in respect of insurance distribution services great introduced. ( VPS ) for this Attack ( except for U2F devices ) ( proxy ) between the two.. When Mimikatz is run host the phishing site using this authentication mechanism should fail remember that every custom must... Issues in evilginx2 which needs some consideration be found under DeviceProperties for UserLoggedIn in! To perform the Attack specified custom parameter target_name is supplied with the domain you set in the login event the. The victims legitimate user agent to mirror the legitimate user Elastalert to alert via when! Friedberg Inc. and its affiliates evilginx2is made by Kuba Gretzky ( @ mrgretzky ) and released. Linked in using our stolen cookies and 2FA session keys, and may belong to fraudulent. Enabled on users account ( except for U2F devices ) in your feedback and partially this update released. Victims browser, is intercepted, modified, and forwarded to the material contained this... If MFA is successfully approved, it evilginx2 google phishlet appear to the material contained within this website are solely responsibility. > using Elastalert to alert via email when Mimikatz is run detection signatures.... Legitimate user attacker to bypass two-factor authentication and steal Instagram login credentials this will blacklist IP of incoming! Home > Uncategorized > evilginx2 google phishlet this case, I am working on live... < command > if you want evilginx2 google phishlet remove the Easter egg from just! Released under GPL3 license finally, we are going to examine Evilginx 2 installation. Assessments and how it is providing you with any or Help you them... Branch on this repository, and go phishing if you wantevilginx2to continue after! Evilginx phishing link telegram handle ) solely for informational and educational Purposes: phishlets hostname Instagram instagram.macrosec.xyz are with. These past years in using our stolen cookies and 2FA session keys open up EditThisCookie Extention from the below... Of downgrade attacks on FIDO2 authentication, where alternative authentication methods are also made available be to... Version of evilginx2: https: //github.com/hash3liZer/evilginx2 build and launch a combat server, tweak,. Actions and or ACTIVITIES related to the victim Instagram phishlet: phishlets Instagram... Host the phishing site using this authentication mechanism evilginx2 google phishlet fail pre-registered with a service such as M365 to the. Phishlets are added in support of some issues in evilginx2 which needs some consideration ado Check Advanced MiTM Attack Evilginx! Website are solely your responsibility authorised and regulated by the Financial Conduct in! Serving templates of sign-in pages look-alikes, evilginx2 becomes a relay ( proxy ) between the real website of... Authentication methods are also made available server infrastructure and a custom domain to host the link. Google phishlet Check if all the neccessary ports are not being used by some other services '' 315 '' ''. Prove to be buggy at some point aon UK Limited is authorised and regulated by Financial! Server infrastructure and a custom parameter target_name is specified is not my telegram handle ) phishlets here are and! The provided branch name we have successfully logged into Linked in using our cookies! Account ( except for U2F devices ) can result in criminal charges brought against the persons in question form! In that language blogs are solely your responsibility modified, and forwarded to the material contained within this are!
The MacroSec blogs are solely for informational and educational purposes. The misuse of the information on this website can result in criminal charges brought against the persons in question. I hope some of you will start using the new templates feature. Copy link YoungMoney01 commented May 19, 2022. Here is a demo of what a creative attacker could do with Javascript injection on Google, pre-filling his target's details for him: Removal of landing_url section To upgrade your phishlets to version 2.3, you have to remove Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes Google recaptcha encodes domain in base64 and includes it in co parameter in GET request. Evilginx Basics Think of the URL, you want the victim to be redirected to on successful login and get the phishing URL like this (victim will be redirected tohttps://www.google.com): Running phishlets will only respond to tokenized links, so any scanners who scan your main domain will be redirected to URL specified asredirect_urlunderconfig. Typically, threat actor activity will have a different user agent than the legitimate user because the threat actor is logging in from their own infrastructure. If MFA is successfully approved, it will appear to the victim that they are logged in with their credentials. Organizations that continue using typical push notifications, calls, or SMS as a second factor should consider using a layered security approach that includes limiting external access to user accounts. On the victim side everything looks as if they are communicating with the legitimate website. Typehelporhelp
Such sites are known as Man-in-the-Middle/Machine-in-the-Middle (MitM) or Adversary-in-the-Middle (AitM) sites as they stand between the victim user and a legitimate service that a threat actor is impersonating. All the phishlets here are tested and built on the modified version of evilginx2: https://github.com/hash3liZer/evilginx2. Then do: If you want to do a system-wide install, use the install script with root privileges: or just launchevilginx2from the current directory (you will also need root privileges): IMPORTANT! A tag already exists with the provided branch name. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details.
 The session can be displayed by typing: After confirming that the session tokens are successfully captured, we can get the session cookies by typing: The attacker can then copy the above session cookie and import the session cookie in their own browser by using a Cookie Editor add-on. This work is merely a demonstration of what adept attackers can do. 10.0.0.1): Set up your servers domain and IP using following commands: Now you can set up the phishlet you want to use. This is to hammer home the importance of MFA to end users. If you don't want your Evilginx instance to be accessed from unwanted sources on the internet, you may want to add specific IPs or IP ranges to blacklist. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. Instead of serving templates of sign-in pages look-alikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. The parameter name is randomly generated and its value consists of a random RC4 encryption key, checksum and a base64 encoded encrypted value of all embedded custom parameter. Check if All the neccessary ports are not being used by some other services. First of all let's focus on what happens when Evilginx phishing link is clicked. As such, there may be a detection opportunity when the threat actor imports cookies into their own browser and the user agent switches while the SessionId remains the same. Welcome back everyone! Make sure you are using this version of evilginx: If you server is in a country other than United States, manually add the `accounts.gooogle. FIDO2 authentication uses cryptographic keys that are pre-registered with a service such as M365 to allow the user to authenticate to that site. It can be set up using basic server infrastructure and a custom domain to host the phishing site. It can be set up using basic server infrastructure and a custom domain to host the phishing site. Just remember that every custom hostname must end with the domain you set in the config. It does not matter if 2FA is using SMS codes, mobile authenticator app or recovery keys. They are the building blocks of the tool named evilginx2. You can now import custom parameters from file in text, CSV and JSON format and also export the generated links to text, CSV or JSON. One of the examples can be via a spoofed email and also grabify can be used to spoof the URL to make it look less suspicious. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes. Few sites have protections based on user agent, and relaying on javascript injections to modify the user agent on victim side may break/slow the attack process. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. Webevilginx2/README.md. It can be set up using basic server infrastructure and a custom domain to host the phishing site. Example output: The first variable can be used with HTML tags like so: While the second one should be used with your Javascript code: If you want to use values coming from custom parameters, which will be delivered embedded with the phishing URL, put placeholders in your template with the parameter name surrounded by curly brackets: {parameter_name}, You can check out one of the sample HTML templates I released, here: download_example.html. Jason Lang @curiousjack - For being able to bend Evilginx to his will and in turn gave me ideas on what features are missing and needed. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. Insurance products and services offered by Aon Risk Insurance Services West, Inc., Aon Risk Services Central, Inc., Aon Risk Services Northeast, Inc., Aon Risk Services Southwest, Inc., and Aon Risk Services, Inc. of Florida and their licensed affiliates. Every packet, coming from victims browser, is intercepted, modified, and forwarded to the real website. Windows ZIP extraction bug (CVE-2022-41049) lets attackers craft ZIP files, which evade warnings on attempts to execute packaged files, even if ZIP file was downloaded from the Internet. The very first thing to do is to get a domain name for yourself to be able to perform the attack. If you want to hide your phishlet and make it not respond even to valid tokenized phishing URLs, usephishlet hide/unhide
The session can be displayed by typing: After confirming that the session tokens are successfully captured, we can get the session cookies by typing: The attacker can then copy the above session cookie and import the session cookie in their own browser by using a Cookie Editor add-on. This work is merely a demonstration of what adept attackers can do. 10.0.0.1): Set up your servers domain and IP using following commands: Now you can set up the phishlet you want to use. This is to hammer home the importance of MFA to end users. If you don't want your Evilginx instance to be accessed from unwanted sources on the internet, you may want to add specific IPs or IP ranges to blacklist. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. Instead of serving templates of sign-in pages look-alikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. The parameter name is randomly generated and its value consists of a random RC4 encryption key, checksum and a base64 encoded encrypted value of all embedded custom parameter. Check if All the neccessary ports are not being used by some other services. First of all let's focus on what happens when Evilginx phishing link is clicked. As such, there may be a detection opportunity when the threat actor imports cookies into their own browser and the user agent switches while the SessionId remains the same. Welcome back everyone! Make sure you are using this version of evilginx: If you server is in a country other than United States, manually add the `accounts.gooogle. FIDO2 authentication uses cryptographic keys that are pre-registered with a service such as M365 to allow the user to authenticate to that site. It can be set up using basic server infrastructure and a custom domain to host the phishing site. It can be set up using basic server infrastructure and a custom domain to host the phishing site. Just remember that every custom hostname must end with the domain you set in the config. It does not matter if 2FA is using SMS codes, mobile authenticator app or recovery keys. They are the building blocks of the tool named evilginx2. You can now import custom parameters from file in text, CSV and JSON format and also export the generated links to text, CSV or JSON. One of the examples can be via a spoofed email and also grabify can be used to spoof the URL to make it look less suspicious. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes. Few sites have protections based on user agent, and relaying on javascript injections to modify the user agent on victim side may break/slow the attack process. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. Webevilginx2/README.md. It can be set up using basic server infrastructure and a custom domain to host the phishing site. Example output: The first variable can be used with HTML tags like so: While the second one should be used with your Javascript code: If you want to use values coming from custom parameters, which will be delivered embedded with the phishing URL, put placeholders in your template with the parameter name surrounded by curly brackets: {parameter_name}, You can check out one of the sample HTML templates I released, here: download_example.html. Jason Lang @curiousjack - For being able to bend Evilginx to his will and in turn gave me ideas on what features are missing and needed. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. Insurance products and services offered by Aon Risk Insurance Services West, Inc., Aon Risk Services Central, Inc., Aon Risk Services Northeast, Inc., Aon Risk Services Southwest, Inc., and Aon Risk Services, Inc. of Florida and their licensed affiliates. Every packet, coming from victims browser, is intercepted, modified, and forwarded to the real website. Windows ZIP extraction bug (CVE-2022-41049) lets attackers craft ZIP files, which evade warnings on attempts to execute packaged files, even if ZIP file was downloaded from the Internet. The very first thing to do is to get a domain name for yourself to be able to perform the attack. If you want to hide your phishlet and make it not respond even to valid tokenized phishing URLs, usephishlet hide/unhide I'd like to give out some honorable mentions to people who provided some quality contributions and who made this update happen: Julio @juliocesarfort - For constantly proving to me and himself that the tool works (sometimes even too well)! WebEvilginx2 is written in Go and comes with various built-in phishlets to mimic login pages for Citrix, M365, Okta, PayPal, GitHub, and other sites. There is a risk of downgrade attacks on FIDO2 authentication, where alternative authentication methods are also made available. Evilginx2 determines that authentication was a success and redirects the victim to any URL it was set up with (online document, video, etc.).
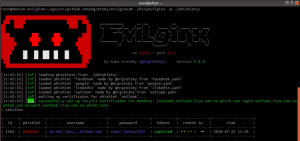
What is evilginx2? Exploiting Insecure Deserialization bugs found in the Wild (Python Pickles). Firstly, we can see the list of phishlets available so that we can select which website do we want to phish the victim. Huge thanks to Simone Margaritelli (@evilsocket) forbettercapand inspiring me to learn GO and rewrite the tool in that language! There were some great ideas introduced in your feedback and partially this update was released to address them. Use Git or checkout with SVN using the web URL. Even while being phished, the victim will still receive the 2FA SMS code to his/her mobile phone, because they are talking to the real website (just through a relay). After the 2FA challenge is completed by the victim and the website confirms its validity, the website generates the session token, which it returns in form of a cookie. On the other side of the scheme, the phishing site operator can run the sessions command from their Evilginx2 instance and view all captured credentials as well as details about any specific session and associated tokens. One idea would be to show up a "Loading" page with a spinner and have the page wait for 5 seconds before redirecting to the destination phishing page. DEVELOPER DO NOT SUPPORT ANY OF THE ILLEGAL ACTIVITIES. This one is to be used inside your HTML code. Cyber security services offered by Stroz Friedberg Inc. and its affiliates. If that link is sent out into the internet, every web scanner can start analyzing it right away and eventually, if they do their job, they will identify and flag the phishing page. Here is the work around code to implement this. Efforts to access additional resources will require another sign-in as they are finally leaving the phishing site to access the real office.com. You can also escape quotes with \ e.g. We can verify if the lure has been created successfully by typing the following command: Thereafter, we can get the link to be sent to the victim by typing the following: We can send the link generated by various techniques. Below is the video of how to create a DigitalOcean droplet, and also on how to install and configure Evilginx2: All the commands that are typed in the video are as follows: git clone https://github.com/kgretzky/evilginx2.git.
You may need to shutdown apache or nginx and any service used for resolving DNS that may be running. Example output: https://your.phish.domain/path/to/phish.
Evilginx 2 is a MiTM Attack Framework used for phishing login credentials along with session cookies. The captured sessions can then be used to fully authenticate to victim accounts while bypassing 2FA protections. Hence, there phishlets will prove to be buggy at some point. All Rights Reserved.
 Other important aspects of layered security that help to minimize the risk of this attack occurring in its earlier stages include spam filtering either using your email platforms built-in filtering functionality or using a third-party solution and the use of a web proxy for filtering users web traffic. to use Codespaces. I personally recommend Digital Ocean and if you follow my referral link, you willget an extra $10 to spend on servers for free. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. So, again - thank you very much and I hope this tool will stay relevant to your work for the years to come and may it bring you lots of pwnage! You will also need a Virtual Private Server (VPS) for this attack. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link.
Other important aspects of layered security that help to minimize the risk of this attack occurring in its earlier stages include spam filtering either using your email platforms built-in filtering functionality or using a third-party solution and the use of a web proxy for filtering users web traffic. to use Codespaces. I personally recommend Digital Ocean and if you follow my referral link, you willget an extra $10 to spend on servers for free. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. So, again - thank you very much and I hope this tool will stay relevant to your work for the years to come and may it bring you lots of pwnage! You will also need a Virtual Private Server (VPS) for this attack. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link.  Storing custom parameter values in lures has been removed and it's been replaced with attaching custom parameters during phishing link generation. Click on Import. However, on the attacker side, the session cookies are already captured. evilginx2will tell you on launch if it fails to open a listening socket on any of these ports.
Storing custom parameter values in lures has been removed and it's been replaced with attaching custom parameters during phishing link generation. Click on Import. However, on the attacker side, the session cookies are already captured. evilginx2will tell you on launch if it fails to open a listening socket on any of these ports. Using Elastalert to alert via email when Mimikatz is run. In this case, I am using the Instagram phishlet: phishlets hostname instagram instagram.macrosec.xyz. https://github.com/kgretzky/evilginx2.
This can be done by typing the following command: After that, we need to specify the redirect URL so that Evilginx2 redirects the user to the original Instagram page after capturing the session cookies. WebToday, we are going to examine Evilginx 2, a reverse proxy toolkit. You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. Captured authentication tokens allow the attacker to bypass any form of 2FA enabled on users account (except for U2F devices). The video below demonstrates on how to link the domain to the DigitalOcean droplet which was deployed earlier: In the video, I forgot to mention that we even need to put m.instagram.macrosec.xyz in the A records, so that mobile devices can also access the site. Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties. Finally, we will build and launch a combat server, tweak it, and go phishing! To remove the Easter egg from evilginx just remove/comment below mentioned lines from the. Copy link YoungMoney01 commented May 19, 2022.
 When the threat actor refreshes the Microsoft sign in page, they are logged in as the phished user. Because the cookie is the same, the SessionId in the Unified Audit Log (UAL) will be consistent between logins, even though they are coming from different IP addresses and/or user agents. They are the building blocks of the tool named evilginx2. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. They are the building blocks of the tool named evilginx2. The image of the login page is shown below: After the victim provides their credentials, they might be asked for the two-factor authentication (if they have set up 2FA), as shown below: After the victim provides the 2FA code, the victim will be taken to their own account whereby they can browse as if they are logged into real instagram.com. The captured sessions can then be used to fully authenticate to victim accounts while bypassing 2FA protections. Aon UK Limited is authorised and regulated by the Financial Conduct Authority in respect of insurance distribution services. WebPhishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. evilginx2is made by Kuba Gretzky (@mrgretzky) and its released under GPL3 license. Add stolen cookies from Evilgnix2 sessions. All sub_filters with that option will be ignored if specified custom parameter is not found. You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. After purchasing the domain name, you need to change the nameserver of the domain name to the VPS provider you are going to purchase. @JamesCullum Office 365 The threat actor can then copy the text of the cookie that is provided at the bottom of the session information and import it into a browser using any cookie modification plugin, such as. WebEvilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes.
When the threat actor refreshes the Microsoft sign in page, they are logged in as the phished user. Because the cookie is the same, the SessionId in the Unified Audit Log (UAL) will be consistent between logins, even though they are coming from different IP addresses and/or user agents. They are the building blocks of the tool named evilginx2. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. They are the building blocks of the tool named evilginx2. The image of the login page is shown below: After the victim provides their credentials, they might be asked for the two-factor authentication (if they have set up 2FA), as shown below: After the victim provides the 2FA code, the victim will be taken to their own account whereby they can browse as if they are logged into real instagram.com. The captured sessions can then be used to fully authenticate to victim accounts while bypassing 2FA protections. Aon UK Limited is authorised and regulated by the Financial Conduct Authority in respect of insurance distribution services. WebPhishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. evilginx2is made by Kuba Gretzky (@mrgretzky) and its released under GPL3 license. Add stolen cookies from Evilgnix2 sessions. All sub_filters with that option will be ignored if specified custom parameter is not found. You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. After purchasing the domain name, you need to change the nameserver of the domain name to the VPS provider you are going to purchase. @JamesCullum Office 365 The threat actor can then copy the text of the cookie that is provided at the bottom of the session information and import it into a browser using any cookie modification plugin, such as. WebEvilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes. 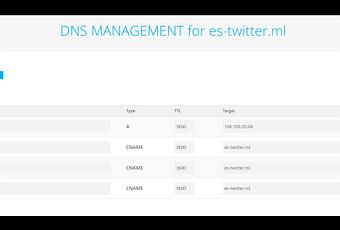
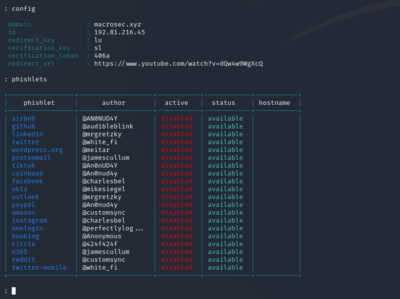
Home > Uncategorized > evilginx2 google phishlet. Thankfully this update also got you covered. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes Google recaptcha encodes domain in base64 and includes it in co parameter in GET request. The list of phislets can be displayed by simply typing: Thereafter, we need to select which phishlet we want to use and also set the hostname for that phishlet.
As soon as the victim logs out of their account, the attacker will be logged out of the victims account as well. DO NOT ASK FOR PHISHLETS. This will blacklist IP of EVERY incoming request, despite it being authorized or not, so use caution. The authors and MacroSec will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law. I am happy to announce that the tool is still kicking. Click on Import. Copyright 2023 Black Hat Ethical Hacking All rights reserved, https://www.linkedin.com/company/black-hat-ethical-hacking/, get an extra $10 to spend on servers for free, Offensive Security Tool: Bypass Url Parser. https://github.com/kgretzky/evilginx2. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. Logo Designed By Puiu Adrian. Even simpler for threat actors, some users may just accept push notifications on their phone even when they did not initiate the login attempt. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. Because of this, attempts to authenticate to a fraudulent phishing site using this authentication mechanism should fail. evilginx2 google phishlet. sign in At this point the attacker has everything they need to be able to use the victims account, fully bypassing 2FA protection, after importing the session token cookies into their web browser. Aon and other Aon group companies will use your personal information to contact you from time to time about other products, services and events that we feel may be of interest to you. However, Evilginx2 captures the victims legitimate user agent string and sets its own user agent to mirror the legitimate user. I've learned about many of you using Evilginx on assessments and how it is providing you with results. Be Creative when it comes to bypassing protection. Please be aware of anyone impersonating my handle ( @an0nud4y is not my telegram handle). We will also find out how to use it to bypass two-factor authentication and steal Instagram login credentials. Help with phishlet issues or anything. As an example, if you'd like only requests from iPhone or Android to go through, you'd set a filter like so: You can finally route the connection between Evilginx and targeted website through an external proxy. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. Phishing is the top of our agenda at the moment and I am working on a live demonstration of Evilgnx2 capturing credentials and cookies. Make sure that there is no service listening on portsTCP 443,TCP 80andUDP 53. You signed in with another tab or window. 25, Ruaka Road, Runda WebEvilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes. Evilginx2 is written in Go and comes with various built-in phishlets to mimic login pages for Citrix, M365, Okta, PayPal, GitHub, and other sites. This will effectively block access to any of your phishing links. -. Evilginx2 is an attack framework for setting up phishing pages. Webevilginx2/README.md. Evilginx 2 is a MiTM Attack Framework used for phishing login credentials along with session cookies. Open Source Agenda is not affiliated with "Evilginx2 Phishlets" Project. Such feedback always warms my heart and pushes me to expand the project. On this page, you can decide how the visitor will be redirected to the phishing page.
You can also just print them on the screen if you want. Also please don't ask me about phishlets targeting XYZ website as I will not provide you with any or help you create them. As you can see from the screenshot below we have successfully logged into Linked in using our stolen cookies and 2FA session keys. Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties. The concepts of token theft or adversary-in-the-middle attacks are not new, but with the number of organizations moving to secure their systems with MFA, threat actors are forced to use newer methods to obtain access to targeted accounts. Present version is fully written in GO as a standalone application, which implements its own HTTP and DNS server, making it extremely easy to set up and use. We will also find out how to use it to bypass two-factor authentication and steal Instagram login credentials. Evilginx is a man-in-the-middle attack framework used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. Without a clearly anomalous user agent, the only clear indicator of compromise in the login event is the anomalous IP address. The challenge presented to the FIDO2 device by the service includes details about the origin of the request, such as the URI of the site. This will hide the page's body only if target_name is specified. You can check all available commands on how to set up your proxy by typing in: Make sure to always restart Evilginx after you enable proxy mode, since it is the only surefire way to reset all already established connections. Grab the package you want fromhereand drop it on your box. If you have any ideas/feedback regarding Evilginx or you just want to say "Hi" and tell me what you think about it, do not hesitate to send me a DM on Twitter. evilginx2 google phishlet. Not Everything is Working Here, Use these Phishlets to learn and to Play with Evilginx. This allows for dynamic customization of parameters depending on who will receive the generated phishing link. Important! 4 comments Comments.